Cloud computing has become the backbone of modern business operations. Organizations are increasingly migrating their workloads, applications, and data to the cloud to leverage its scalability, flexibility, and cost-efficiency. However, with this shift comes a new set of challenges, particularly in ensuring cloud data protection, security, and compliance of cloud environments. This is where Cloud Security Posture Management (CSPM) comes into play.
CSPM is a critical component of cloud security that helps organizations identify and remediate risks, enforce compliance, and maintain a strong security posture in their cloud infrastructure. In this blog, we’ll explore what CSPM is, why it’s essential, and how organizations can use it to stay compliant with industry regulations and standards.
What is Cloud Security Posture Management (CSPM)?
Cloud Security Posture Management (CSPM) refers to a set of tools, processes, and practices designed to continuously monitor, assess, and improve the security posture of cloud environments. CSPM solutions provide visibility into cloud assets, detect misconfigurations, enforce security policies, and ensure compliance with regulatory requirements.
Why Is CSPM Important?
Cloud services and cloud-based applications provide significant benefits in terms of productivity and flexibility. However, their accessibility over the internet and widespread availability also introduce heightened cybersecurity risks, such as data breaches. Despite efforts like security awareness training, vulnerabilities persist, putting sensitive data at risk.
Organizations often rely on managed cloud security services alongside CSPM to address cloud security challenges effectively. IT security and business leaders are continually tackling the following challenges:

- Misconfigurations in cloud infrastructure, which can lead to massive data exposures, resulting in legal consequences and financial damage.
- Ensuring continuous cloud security compliance for cloud applications and workloads, a task that traditional on-premises security tools and methods cannot effectively handle.
- Cloud governance issues, including limited visibility, improper permissions, weak policy enforcement, and a lack of understanding of cloud security controls, which escalate as cloud adoption grows.
While data breaches attract the most attention and cause the most harm, misconfigurations remain a top cause, accounting for over 20% of breaches according to Verizon’s 2023 Data Breach Investigations Report. Additionally, web applications are consistently among the top three attack vectors across industries.
To mitigate these risks, an effective Cloud Security Posture Management (CSPM) solution is essential. It offers automated visibility, real-time alerts, and enforcement mechanisms to safeguard sensitive data and infrastructure from the inherent dangers of cloud environments.
A MUST READ – 5 Critical Vulnerabilities in Cloud Deployments and How to Fix Them
How CSPM Helps Organizations Stay Compliant
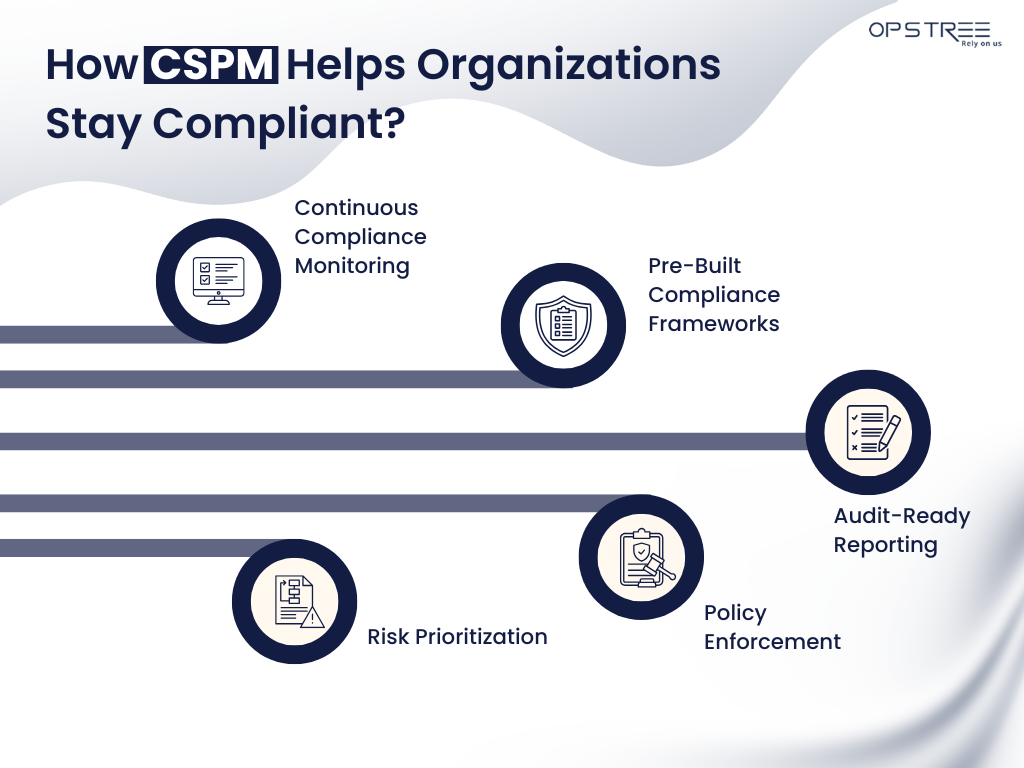
Compliance and cloud data protection are top priorities for organizations operating in regulated industries. Non-compliance can result in hefty fines, reputational damage, and even legal action. CSPM plays a vital role in helping organizations stay compliant by providing the following capabilities:
-
Continuous Compliance Monitoring
CSPM tools continuously monitor cloud environments to ensure continuous compliance in cloud, adhering to regulatory standards and internal policies. These cloud security automation solutions provide real-time alerts when deviations occur, enabling organizations to take corrective action immediately.
-
Pre-Built Compliance Frameworks
Most CSPM solutions come with pre-configured compliance templates for standards like GDPR, HIPAA, PCI DSS, and NIST. These templates simplify the process of assessing and maintaining compliance.
-
Audit-Ready Reporting
CSPM tools generate detailed reports that demonstrate compliance with regulatory requirements. These reports are invaluable during audits, as they provide evidence of due diligence and adherence to standards.
-
Policy Enforcement
CSPM allows organizations to define and enforce security policies across their cloud environments. For example, policies can be created to ensure encryption is enabled for all storage buckets or that multi-factor authentication (MFA) is enforced for user accounts.
-
Risk Prioritization
CSPM tools assess the severity of risks and prioritize them based on their potential impact. This helps organizations focus on addressing the most critical issues first, ensuring compliance and reducing the likelihood of breaches.
DID YOU KNOW?
The global cloud security posture management market is projected to expand from USD 4.2 billion in 2022 to USD 8.6 billion by 2027, growing at a CAGR of 15.3%.
Real-World Example
Capital One Data Breach (2019)
What Happened?
Capital One suffered a massive data breach in 2019, exposing the personal information of over 100 million customers. The breach occurred due to a misconfigured web application firewall (WAF) in their AWS environment.
How CSPM Could Have Helped
A robust CSPM solution could have detected the misconfiguration in real-time, enforced proper security policies, and prevented unauthorized access to sensitive data.
Lesson Learned
This incident underscores the importance of continuous compliance monitoring and automated risk detection in cloud environments.
Best Practices for Implementing CSPM
To maximize the benefits of CSPM and ensure compliance, organizations should follow these best practices:
-
Choose the Right CSPM Solution
Not all CSPM tools are created equal. When selecting a CSPM solution, consider factors like multi-cloud support, ease of integration, automation capabilities, and the availability of pre-built compliance templates.
-
Conduct a Cloud Asset Inventory
Start by gaining visibility into all cloud assets, including virtual machines, storage buckets, databases, and user accounts. A comprehensive inventory is the foundation of effective CSPM.
-
Define and Enforce Security Policies
Establish clear security policies for your cloud environment and use CSPM tools to enforce them. Regularly review and update these policies to address emerging threats and regulatory changes.
-
Automate Remediation
Leverage the automation capabilities of CSPM tools to quickly remediate misconfigurations and security issues. Cloud security automation solutions help reduce human error and ensure timely resolution of problems, strengthening overall security posture.
-
Educate and Train Your Team
Ensure your team understands the importance of cloud security and compliance. Provide training on CSPM tools and best practices to empower them to effectively manage your cloud environment.
-
Regularly Review and Update Compliance Requirements
Regulatory requirements are constantly evolving, making continuous compliance in cloud a crucial priority. Stay informed about changes to compliance standards and update your CSPM policies and configurations accordingly.
-
Conduct Regular Audits
Perform regular audits of your cloud environment to identify gaps in security and compliance. Use the insights gained from these audits to improve your CSPM strategy.
How Can OpsTree Help You with CSPM?
At OpsTree, we understand the complexities of managing cloud security and compliance in today’s dynamic environment. Our expert team provides tailored Cloud Security Posture Management (CSPM) solutions to help you identify risks, enforce policies, and ensure cloud security compliance across multi-cloud platforms.
With our deep expertise in cloud technologies and security frameworks, we offer end-to-end support, from implementation to continuous monitoring, ensuring your cloud environment remains secure, compliant, and optimized for business success.
Frequently Asked Questions
-
What is Cloud Security Posture Management (CSPM)?
A. Cloud Security Posture Management (CSPM) is a set of tools and practices that continuously monitor cloud environments to identify risks, enforce security policies, and ensure cloud security compliance. It helps prevent misconfigurations and enhances cloud data protection.
2. Why is CSPM important for cloud security compliance?
A. CSPM is essential for maintaining continuous compliance in cloud environments by detecting vulnerabilities, enforcing policies, and automating remediation. It ensures organizations meet industry standards like GDPR, HIPAA, and PCI DSS.
3. How does CSPM help prevent cloud misconfigurations?
A. CSPM solutions provide real-time visibility into cloud assets, detect security misconfigurations, and automate remediation. By leveraging cloud security automation solutions, organizations can reduce human errors and enhance security.
4. What are the key features of an effective CSPM solution?
A. An effective CSPM solution includes continuous compliance monitoring, pre-built compliance frameworks, automated risk prioritization, policy enforcement, and audit-ready reporting. Managed cloud security services often integrate CSPM to enhance security posture.
5. How can OpsTree help with Cloud Security Posture Management?
A. OpsTree offers cloud security consulting services to implement and manage CSPM, ensuring cloud security compliance across multi-cloud platforms. Our team provides risk identification, policy enforcement, and continuous monitoring to keep cloud environments secure.
