NGROK
Ngrok is multiplatform tunneling, reverse proxy software that establishes secure tunnels from a public endpoint such as the internet to a locally running network service while capturing all traffic for detailed inspection and replay.
We are using Ngrok to host our Jenkins service (running on port 8080) to public IP.
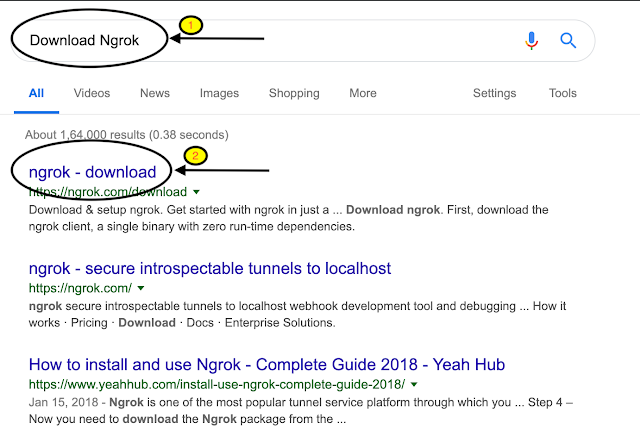
Go to google and search for Download Ngrok.
Either Login with google account or do Ngrok own signup.
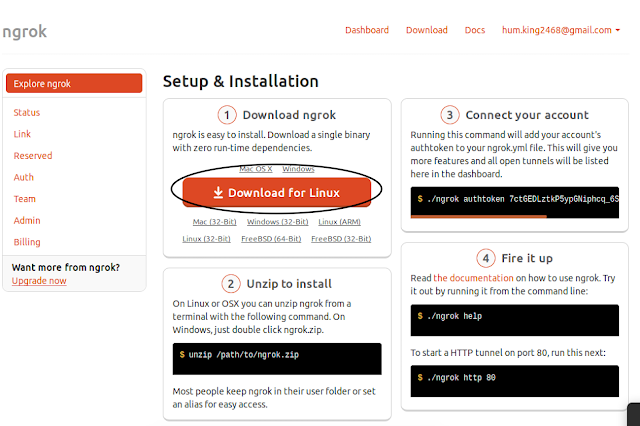
After Logged in Ngrok Download it.
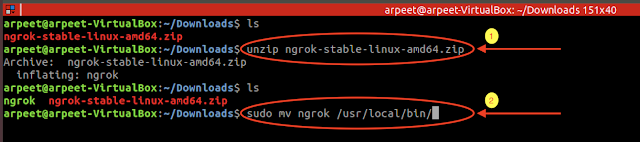
After Download Ngrok, Go to the console and unzip the downloaded zip file and then move it to /usr/local/bin.
Note: Moving part is optional, we do so for accessing ngrok from anywhere.
Go to ngrok UI page , copy the authentication key and paste it.
Note: Remove ” . / ” sign because we moved ngrok file to /usr/local/bin
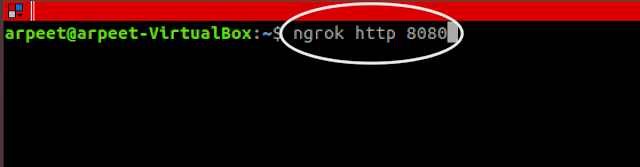
Major configuration for Ngrok is done. Now type the command:
ngrok http 8080
Assuming that Jenkins is running on port 8080.
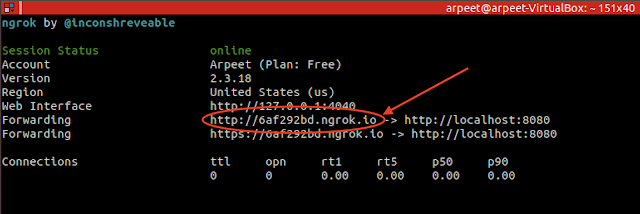
Now Ngrok Host our Jenkins Service to public IP.
Copy this IP, we will use it in the google developer console.
Note: Make this terminal up and running.(don’t do ctrl+c)
Step 2: Setup Google Developer Console
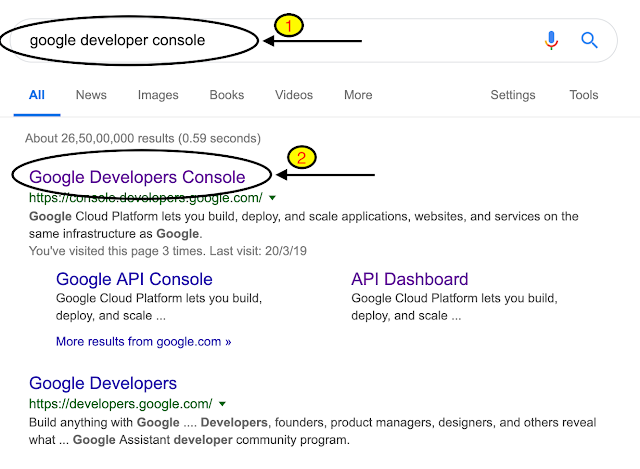
Go to google and search for google developer console.
After sign in into google developer console, we will redirect to Google developer console UI screen.
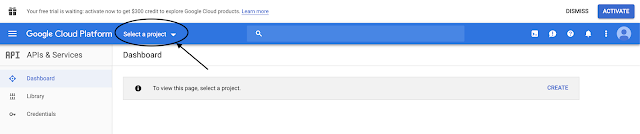
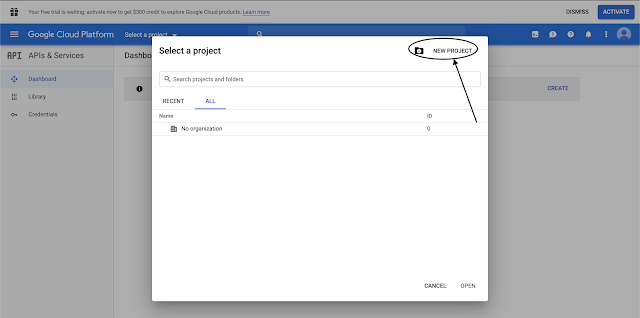
Go to Select a project → New Project
Give Project Name, here I will use “JenkinsGmailAuthentication” and create a project. Creating a project takes 1 or 2 minutes.
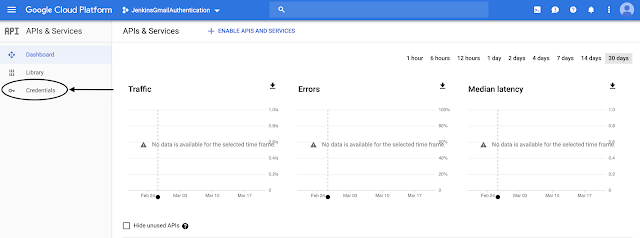
After Project created, we will be redirected to the UI page as shown below. Now click on on the “Credentials” Tab on the left slide bar.
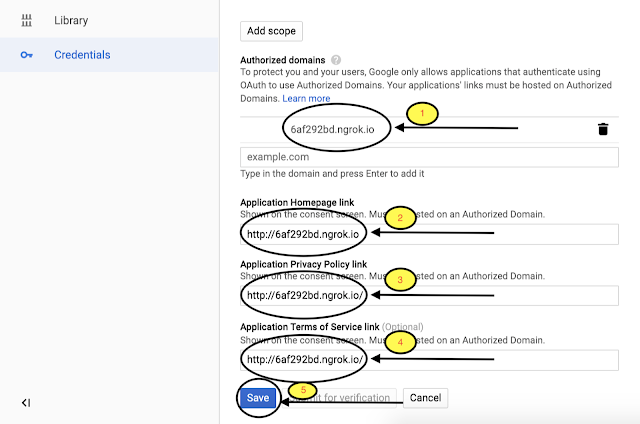
After Go to the OAuth consent screen tab and give the below entries. Here I will give Application name to “JenkinsGmailAuthentication”.
The important part of the Google developer console is Public IP we created using Ngrok. Copy Public IP in Authorized domains and note to remove ” http:// ” in Authorized domains.
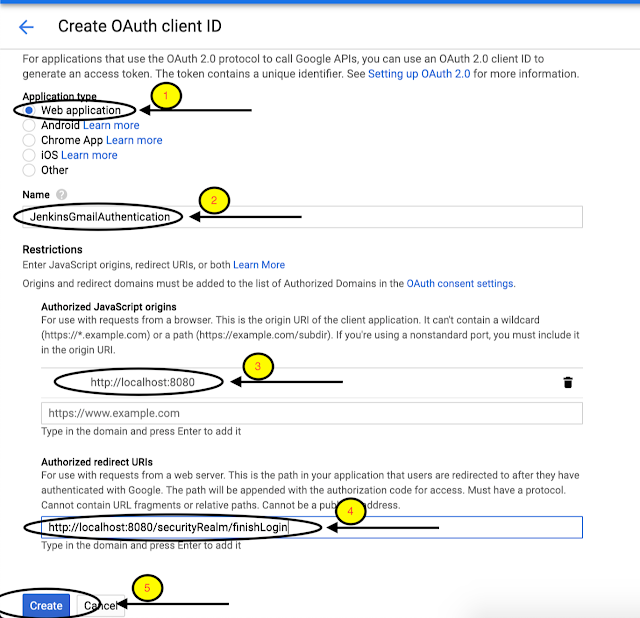
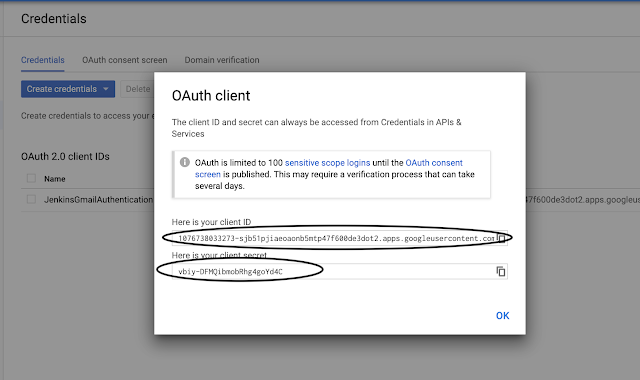
After Setting OAuth consent screen, Go to “Credentials Tab”→ Create Credentials→OAuthClientID
Select Application type as Web Application, give the name “JenkinsGmailAuthentication”.
Major Part of Create Credential has Authorized JavaScript origins and Authorized redirect URIs.
Copy Client ID and Client Secret because we are going to use these in Jenkins.
Step 3: Setup Jenkins
I am assuming that Jenkins is already installed in your system.
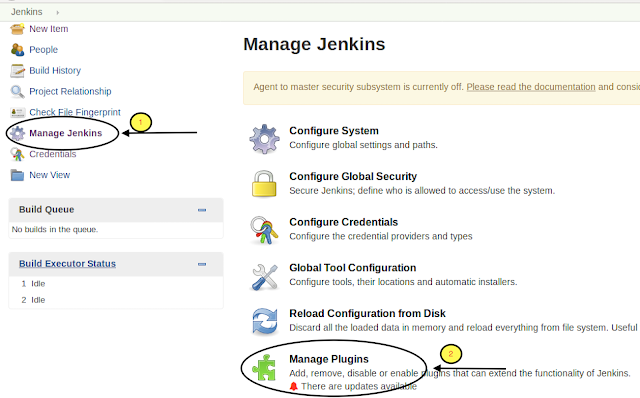
Go to Manage Jenkins → Manage Plugins→ Available
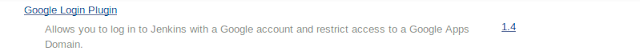
Search for “Google Login Plugin” and add it.
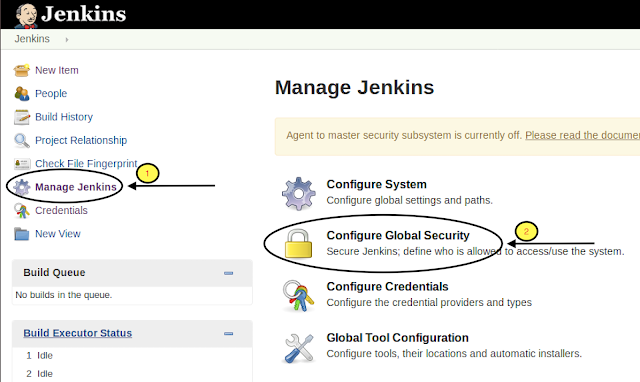
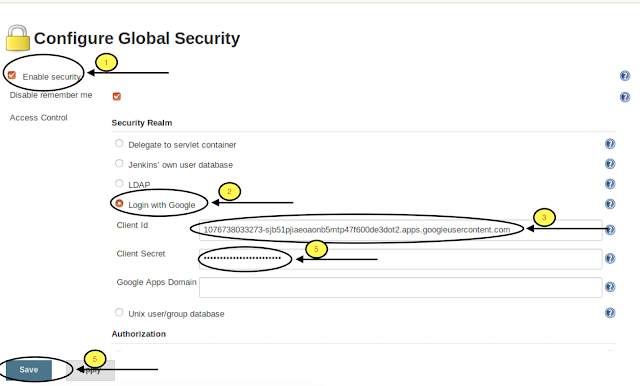
Go to Manage Jenkins → Configure Global Security
The major part of Jenkins Setup is to Configure Global Security.
Check the Enable security → Login with Google and Paste the Client ID and Client secret generated in Create Credential Step and Save.
Up to here, we are done with the Setup part.
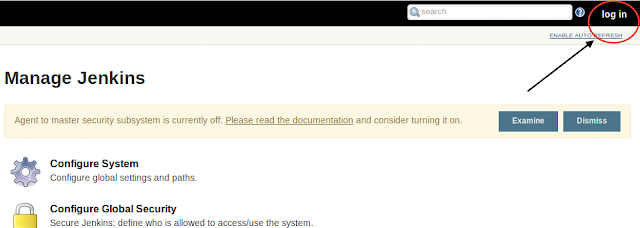
Now Click on login button on Jenkins UI, you will redirect to Gmail for login.
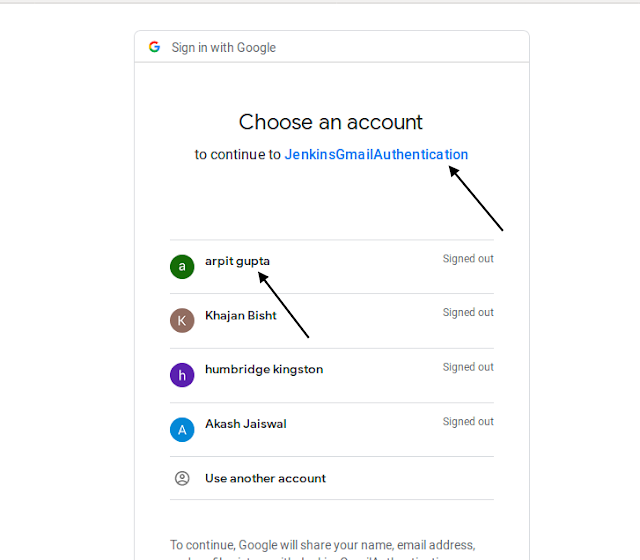
Select the account from which you want to log in.
After selecting Account you will redirect to Jenkins and you are logged in as selected user.
You may be facing a problem when you log in again.
Logout from the current user and login again.
After redirected to Gmail select another user.
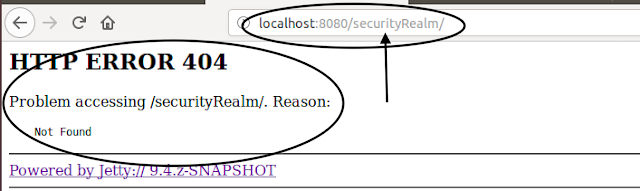
After selecting user you will be redirected to Error Page showing: HTTP ERROR 404.
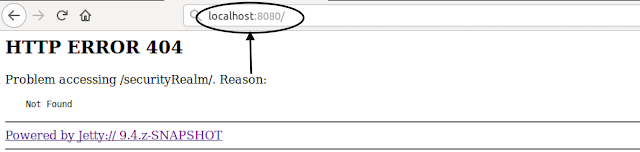
Don’t worry, you have to just remove “securityRealm/” or enter again “localhost:8080”.
You are logged in with the selected user.
So now you know how to do Gmail Authentication between Google developer console and Jenkins when they are not directly reachable to each other.
Here the main bridge between both is Ngrok which host our Privately hosted Jenkins to outer internet.