Introduction
Chef Solo is simple way to begin working with Chef. It is an open source version of the chef-client that allows using cookbooks with nodes without requiring access to a server. Chef Solo runs locally and requires that a cookbook (and any of its dependencies) be on the same physical disk as the node. It is a limited-functionality version of the chef-client and does not support the following:
- Node data storage
- Search indexes
- Centralized distribution of cookbooks
- A centralized API that interacts with and integrates infrastructure components
- Authentication or authorization
- Persistent attributes
Installing chef-client (Pre-requisite : curl )
Login to your box and run the following command to install the chef. Make sure that curl program is available on your box.
curl -L https://www.opscode.com/chef/install.sh | bash
To check if the installation was successful check the version of the installed chef-solo by:
chef-solo -v
wget http://github.com/opscode/chef-repo/tarball/master
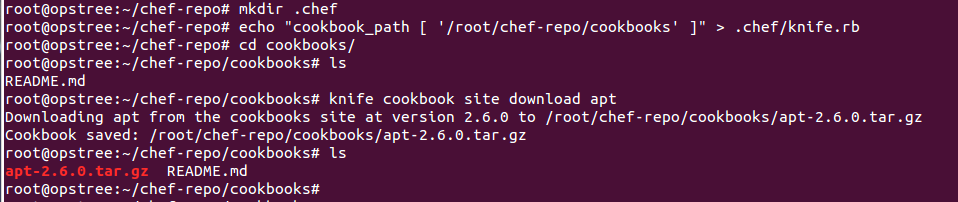
tar zxf master mv opscode-chef-repo-**** chef-repo/ mkdir .chef
echo "cookbook_path ['/root/chef-repo/cookbooks' ]" > .chef/knife.rb
knife cookbook site download apt
cookbook_path [ '/root/chef-repo/cookbooks' ]
role_path [ '/root/chef-repo/roles' ]
environment_path [ ' /root/chef-repo/environments ' ]
data_bag_path [ ' /root/chef-repo/data_bags ' ]
The node.json file sets the run list (and any other node-specific attributes if required).
current_dir = File.expand_path(File.dirname(__FILE__))
file_cache_path "#{current_dir}"
cookbook_path "#{current_dir}/cookbooks"
role_path "#{current_dir}/roles"
data_bag_path "#{current_dir}/data_bags"
{
"run_list": [ "recipe[]" ]
}
In this example i am going to install apt cookbook and the recipe which i am going to use is apt and here is my solo.rb and node.json files looks like
chef-solo -c solo.rb -j node.json How it works:
-
solo.rb configures Chef Solo to look for its cookbooks, roles, and data bags inside the current directory: the Chef repository.
-
Then, Chef Solo just executes a Chef run based on the configuration data found in