Cloud computing has become integral to our daily lives, often in ways we don’t even notice. The cloud has transformed how we manage and access data, from backing up photos on smartphones to sharing files and collaborating on documents. However, the cloud isn’t immune to security risks like any online platform. Cyberattacks targeting cloud data are a real concern and deserve careful attention.
In this blog, we’ll explore the potential vulnerabilities of cloud storage and share actionable steps to protect your data effectively.
What is the Cloud?
The cloud opens up remarkable opportunities for businesses and individuals alike but also introduces security challenges that must not be overlooked. Before exploring strategies for safeguarding data, it’s crucial to understand the concept of cloud computing. At its core, cloud computing allows users to access computing power, storage, and resources remotely through networked infrastructure.
Unlike relying solely on local devices and installations, cloud platforms offer on-demand resources hosted in geographically distributed data centers and accessible via the Internet. This flexibility enables users to scale performance dynamically and access data virtually anywhere.
While this connectivity drives innovation and efficiency, it also emphasizes the need to protect sensitive information. Data security across public networks requires robust encryption and access control measures to maintain confidentiality and integrity.
Cloud storage is just one of the many ways we interact with cloud technology daily. Chances are, you’ve also relied on cloud-powered services in various contexts, such as:
- Cloud computing platforms: Microsoft Azure, Amazon Web Services (AWS)
- Email services: Proton Mail, Gmail
- Social media platforms: Facebook, Twitter
- Online collaboration tools: Google Docs, Microsoft 365
- Video conferencing software: Zoom, Skype
Cloud computing presents a wealth of advantages for businesses. It empowers organizations to adjust their IT resources dynamically, aligning with current demands. Unlike conventional computing platforms, the cloud eliminates the need for hefty upfront investments in physical servers and networking infrastructure, reducing costs and maintenance efforts.
Can Cloud Data be Hacked?
Yes, cloud systems can be vulnerable to hacking. Despite the robust security protocols most cloud service providers implement, no technology is immune to breaches. The safety of your data largely depends on the encryption standards employed by the provider and the overall security measures in place.
Don’t Miss This Blog – Top 10 Lessons Learned from Failed Cloud Migrations: What Went Wrong?
How Can Cloud Data Be Hacked?
Cloud environments can be vulnerable to various types of cyberattacks, and while cloud providers implement strong security measures, there are still risks if proper safeguards are not in place. Here are some common ways cloud systems can be compromised:
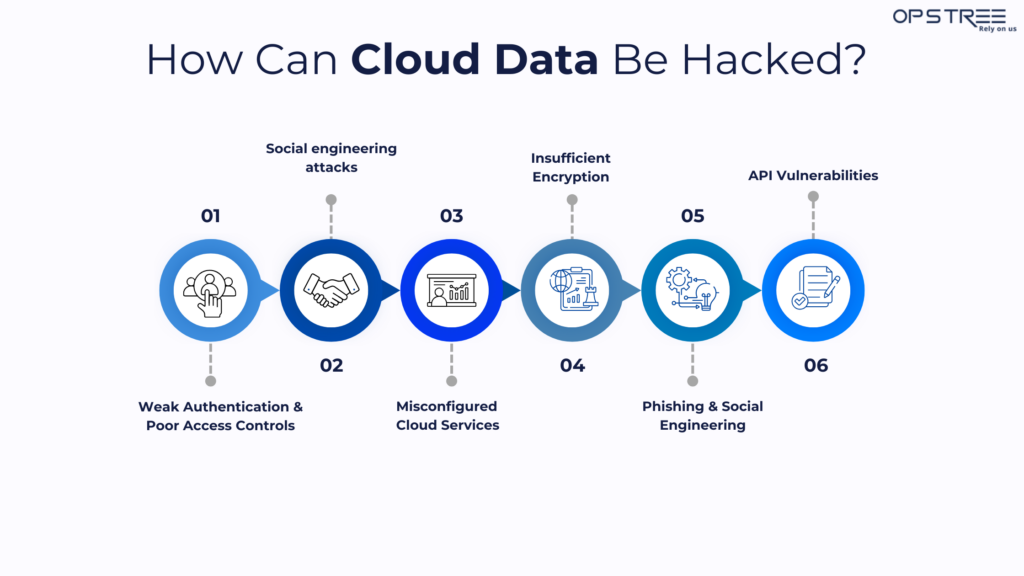
- Weak Authentication & Poor Access Controls
If cloud services rely on weak passwords, lack multi-factor authentication (MFA), or do not implement strict access controls, hackers can gain unauthorized access by brute-forcing credentials or exploiting weak authentication mechanisms.
- Social engineering attacks
Cloud providers are not immune to data breaches, and one common method hackers use to gain access to sensitive information is social engineering. In these attacks, cybercriminals exploit the “human loophole,” manipulating employees to reveal confidential details, which then paves the way for unauthorized access to systems and data.
In November 2022, Dropbox, a well-known cloud storage provider, became a target of a data breach. The incident occurred when an attacker gained access to a Dropbox developer’s GitHub account after falling victim to a phishing scam. As a result, the hacker managed to steal 130 internal code repositories and personal data, including the names and email addresses of Dropbox employees, past and present customers, sales leads, and vendors.
- Misconfigured Cloud Services
Many cloud hacks occur due to misconfigurations in cloud services, such as exposed storage buckets, unsecured APIs, or improper resource permissions. These misconfigurations can allow hackers to access sensitive data or gain control over cloud infrastructure.
- Insufficient Encryption
If sensitive data in the cloud is not encrypted both in transit and at rest, hackers can intercept and steal it. Poor encryption practices or the absence of encryption altogether can make it easier for attackers to access valuable data.
- Phishing & Social Engineering
Hackers often use phishing emails or social engineering techniques to trick cloud service users into giving away their login credentials or other sensitive information. This can lead to unauthorized access to cloud accounts or services.
- API Vulnerabilities
Many cloud platforms offer APIs for integrations, but if these APIs are not secured, attackers can target them. Exploiting API vulnerabilities can allow hackers to manipulate cloud resources or access data.
[ Are you looking: Cloud database management services ]
Stat of the Day
Buckle up! The global Cloud Computing Market is gearing up for a massive surge, leaping from USD 626.4 billion in 2023 to USD 1,266.4 billion by 2028, with a CAGR of 15.1%!
How to Protect Yourself From Cloud Hacking
To bolster cloud security beyond the measures provided by cloud providers, users should implement the following best practices:
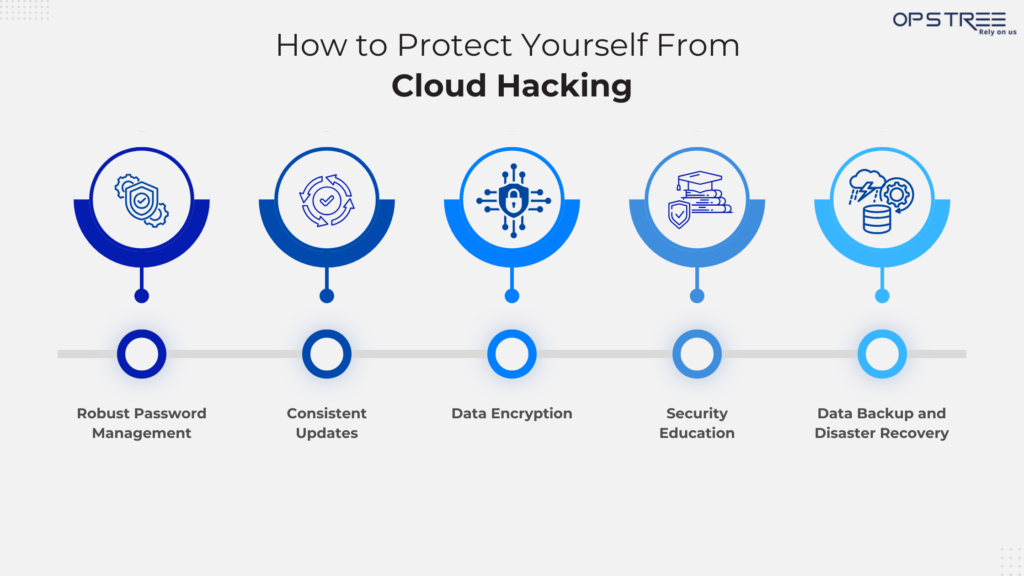
- Robust Password Management: Employ strong, unique passwords for every cloud account. Crucially, multi-factor authentication (MFA) should be enabled whenever possible to add a layer of security.
- Consistent Updates: Maintain up-to-date software and applications by promptly installing the latest security patches and updates. This proactive approach mitigates vulnerabilities and reduces the risk of exploitation.
- Data Encryption: Encrypt sensitive data before uploading it to the cloud. Encryption safeguards data confidentiality by preventing unauthorized access, even if a breach occurs.
- Security Education: Train users on common cloud security threats and best practices for identifying and avoiding them. This reduces the risk of human error and accidental data exposure.
- Data Backup and Disaster Recovery: Regularly back up data and establish robust disaster recovery plans. This ensures business continuity and minimizes the impact of data loss due to cyberattacks, hardware failures, or other unforeseen events.
How Can OpsTree Help You With Cloud Solutions?
We offer a full spectrum of cloud data engineering services, from initial cloud advisory to ongoing support. Our expertise spans all aspects of cloud data engineering, including multi-cloud data engineering and Cloud infrastructure and security.
Whether you need help building a new data lake, optimizing existing data pipelines, or migrating to the cloud, our team of experts can help you achieve your data goals.
Frequently Asked Questions
Q. Can cloud data be hacked?
A. Cloud data can be hacked if the cloud system has vulnerabilities such as weak authentication, poor encryption, or misconfigurations.
Q. What are the common ways cloud systems can be compromised?
A. Common ways include weak authentication, social engineering attacks, misconfigured cloud services, insufficient encryption, phishing, and API vulnerabilities.
Q. How can I protect my data from cloud hacking?
A. To protect your data, use strong passwords, enable multi-factor authentication, encrypt sensitive data, keep software updated, and educate users on security best practices.
Q. What is multi-cloud data engineering?
A. Multi-cloud data engineering involves using multiple cloud providers for data storage and processing, providing flexibility and redundancy and minimizing reliance on a single cloud platform.
Q. How can OpsTree help with cloud data engineering?
A. OpsTree offers comprehensive cloud data engineering services, including cloud advisory, multi-cloud data engineering, and data pipeline optimization, ensuring secure and efficient data management.
