
Context
Let’s first talk about how it all started with and what we achieved.
It’s all started with a healthy discussion with a team where our team members were discussing many aspects of different fields of technology. So, one of our colleagues mentioned OpenVPN. So, we discussed the different working field, architecture, workflow of OpenVPN, in which role of iptables comes into the picture because for Linux architecture, OpenVPN support iptables as it’s primary firewall utility or can say OpenVPN support iptables as it’s a firewall for filtering workflow.
So in-between discussion, I mentioned that I am using iptables in OpenVPN to block traffic for the domain name and it is working fine. So, my colleague asked me about how you implemented & how is it possible to use iptables for domain and they discussed multiple logical explanations like OSI layer support and many other things. So, we decided to do POC of this discussion and try to write-up some blog or points to make clear that is it possible use iptables for the domain name and if not, what are the area that we can cover with iptables for the domain name and try to cover up flaws of this.Description
In short, it depends on the use case & type of chain rule or filters that we are applying.
Basically for those who don’t know, iptable is a firewall program for Linux. Iptable basically monitors & applies a set of rules using tables & these tables contain sets of rules, called chains, that will filter incoming and outgoing data packets. Filters mean blocking & allowing connection according to rule. Iptable is a very flexible firewall utility so we can customize our rules accordingly.
But before going further, let’s discuss some use cases regarding how to setup & why exactly we need domain blocking for any application through iptables. Let’s take some example:
Let’s assume that we are using OpenVPN with iptables as firewall management utility and we already know that iptables is a very flexible utility for managing traffic filter rules.
OpenVPN workflow

In the above diagram, there is an OpenVPN server between the client & the internet, and depends on the configuration, the OpenVPN server filtering traffic request comes from client using iptables firewall utility.
And it’s a very common practice of filtering traffic on any VPN. Most of the time, we apply the iptables rule on ports & IP address. Like, we want to allow only a specific IP address or any specific port rather than allowing full connection and sometimes, we want to block a few ports rather than blocking all connections.
What if someone wants to apply a filter for domain name rather than IP address means we are applying rules on the basis of the domain name. There is no hardcoded option for domain name filtering for iptables utility and we can easily apply iptables rules by replacing the IP address with the domain name. These things has it’s own flaws and we will discuss those flaws later on this blog. Let’s first try to setup some rules.
$ iptables -A FORWARD -s X.X.X.X/8 -d X.X.X.X/X -i tun0 -j DROP
Just replace “X.X.X.X/X” by domain name and it will work as it works for IP address.
$ iptables -A FORWARD -s X.X.X.X/8 -d domainname.com -i tun0 -j DROP
In the above command, we apply iptable filter rule for OpenVPN client network “X.X.X.X./8” which include interface “tun0”, which is virtual Ethernet for OpenVPN and this iptables filter rule dropping all connection for specific domain “domainname.com”. If you will look closely you will see that, it’s the same command as we used for IP address which means we just need to replace the IP address part for the domain name and everything work as it is. Any application that uses iptables as a part of functions like OpenVPN & Linux as Router, DHCP server. We can apply the iptables rule for the domain name as well just like we did for IP address.
Limitations of Iptables for domain name
Now let’s discuss about flaws of iptables for domain name,
With iptable, we can apply rules according to the domain name. There are a few ways we can apply iptable according to the domain name.
First, there is a simple way through which we can apply as we discussed earlier
Example –
$ iptables -A OUTPUT -p tcp -d X.X.X.X/XX -j DROP
$ iptables -A INPUT -p tcp -s X.X.X.X/XX -j DROP
In the above example, we are using the IP address for source & destination but instead, we can also use the domain name to establish by applying rules.
Example –
$ iptables -A INPUT -p tcp -s www.domainname.com -j DROP

$ iptables -A OUTPUT -p tcp -d www.domainname.com -j DROP

But, sometimes these rules does not work as it should be. It is mainly because of iptable deals with the IP addresses.
Output of above iptables command:

Let’s take a case about site [HTTPS/HTTP] protocol:
Single domain with multiple IP’s:
Any domain can have multiple IP addresses & it is not permanent so it can change in the future. But when we apply a set of rules for that specific domain iptable first check if that domain exists or not and after that it resolves the domain and applies the rule to the all IP address of that domain [If the domain contains multiple IP’s]. So, if in any case domain or site IP address changes. iptable rule for that site or domain will out of date or we can say, the rule will have zero effect on that specific domain rule.

Single IP with multiple domains:
When we apply an iptable rule for a specific domain. iptable apply rules to IP address that the domain is attached to. So, because of this, iptable blocks all the domains or sites that are attached to a specific IP address.

In the above diagram, the black line show’s that we applied the rule for “domain1.com” and as we applied the rule for a domain name, the rule applied to the public IP that specific domain is attached to. So, because of this, the user will not be able to access the “domain2.com” site that is hosted on a server whose IP got dropped or blocked by iptable rules on the server and so on.
Most of the time when we are applying rules using the domain name, iptable utility applied rules to CDN URLs and all IP addresses that are attached to a specific domain and very few cases when rule applied to a specific domain.
CDN URL iptables output –

Multiple IP’s iptables output –
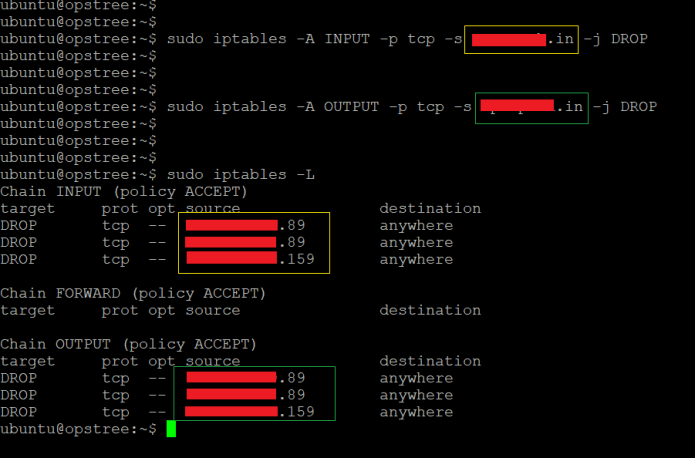
And there are even lots of different examples through which we can examine that using a domain name instead of an IP address is not a good fit for iptable chain filter rules.
String-based filter method
But wait there is another option is a string-based filter,
In a string-based filter, iptable does not apply rules to the specific IP addresses of the domain name but instead, it applies rules to the matching pattern of a string.
Example –
$ iptables -A OUTPUT -p tcp -m string --string domainname.com --algo kmp -j DROP
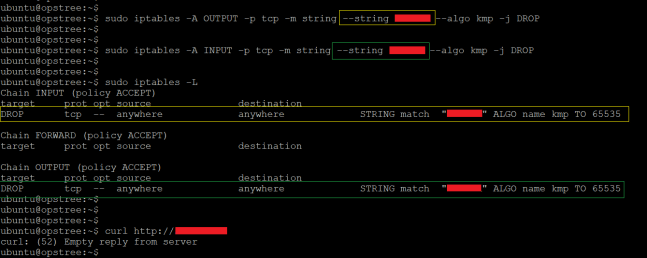
In the above example, iptable utility applies the rule to the “domainname.com” string rather than the IP address. So, next time any URL or packet contains that specific string it will block by iptable filter rules but this filter type that has its own drawback. If somebody uses the IP address directly that would be bypassed.
But, using the IP address to access things, it does not give a guarantee that you can access things that you were only able to access by using the domain name.
Let’s take the example of web protocol [ HTTP/HTTPs ], it depends on the configuration of the server that you are able to access resources of specific domain by single domain or by using an IP address or by both. So, it depends on the server configuration

In the above diagram, we used a string-based filter to block specific domain names, and now using the dig command we are able to get information like “A-record” of that specific domain. As shown in the diagram, we got more than a single IP. So, we will use any of the IP addresses and try to curl the content using the IP address.
Let’s curl using IP address,

As you can see we are unable to access the content of a specific domain using the IP address of that domain. The only resource we can access where server configuration is not proper means the same content or resource able to access by domain or by IP address.
Conclusion
So, the conclusion is iptable works with the domain name but it is not a proper fit for the domain name because there are lots of flaws using iptable for domain name filtering.
So, this is the finding regarding how Iptables work with the domain names but with lots of limitations. If you have any query or point regarding that you want to share or discuss. Please let us know in the comment section.
Opstree is an End to End DevOps solution provider

which is the best proper way for block systemwide filtering like adguard does in windows for linux?